Show HN Today: Discover the Latest Innovative Projects from the Developer Community
 ShowHN Today
ShowHN TodayShow HN Today: Top Developer Projects Showcase for 2025-08-16
SagaSu777 2025-08-17
Explore the hottest developer projects on Show HN for 2025-08-16. Dive into innovative tech, AI applications, and exciting new inventions!
Summary of Today’s Content
Trend Insights
Today's Hacker News highlights a fascinating mix of trends. The focus on system design is a clear signal: developers are thinking about how to build more resilient and scalable applications. This is critical for startups and established companies alike, as it impacts everything from user experience to cost management. Secondly, the discussion surrounding privacy and government control indicates an ongoing need for privacy-respecting technologies. The rise of AI continues to be a dominant theme, with its impact spreading across various sectors. Developers should explore how to integrate AI into their projects responsibly, focusing on ethical considerations. The unexpected use of subscription models in areas like car features highlights a potential monetization strategy that startups may consider. Finally, the increased focus on cybersecurity highlights that protecting data and users should be a top priority for all developers and companies. Embrace the hacker spirit: experiment with new technologies, prioritize user privacy, and build systems that are both innovative and secure. Don't be afraid to challenge the status quo and find creative solutions to complex problems.
Today's Hottest Product
Name
Good system design
Highlight
This post, while not a specific project, emphasizes the importance of robust system design principles. It likely discusses key concepts like scalability, fault tolerance, and efficient data management. Developers can learn how to think strategically about building systems that can handle growth and unexpected issues, ensuring long-term stability and performance.
Popular Category
System Design
Privacy
AI
Popular Keyword
System Design
AI
Privacy
Cybersecurity
Subscription
Technology Trends
The increasing focus on system design best practices for large-scale applications.
The ongoing debate around data privacy and government control.
The application of AI in various fields, from healthcare to development tools.
The use of subscription models in unexpected areas, like car features.
The growing significance of cybersecurity in various industries.
Project Category Distribution
System Design & Software Development (25%)
Privacy & Security (15%)
AI & Machine Learning (10%)
Hardware & Networking (5%)
News & Current Affairs (30%)
Health & Science (5%)
Programming Languages (5%)
Other (5%)
Today's Hot Product List
| Ranking | Product Name | Likes | Comments |
|---|---|---|---|
| 1 | GoodSystemDesignExplorer | 867 | 374 |
| 2 | ChatControl-Buster: A Privacy-Focused Analysis Tool | 422 | 341 |
| 3 | OpenAI Progress Tracker: A Glimpse into AI Advancements | 383 | 321 |
| 4 | Unscalable Scaling: A Pragmatic Approach to Problem Solving | 488 | 202 |
| 5 | Keratin Toothpaste - A Bio-engineered Approach to Dental Care | 422 | 196 |
| 6 | Horsepower Unlocker: A Software-Defined Performance Booster | 176 | 304 |
| 7 | OnionSlice: Optimal Onion Dicing with Computational Geometry | 341 | 130 |
| 8 | IONIQ 5 Patch Payment Analysis Tool | 243 | 198 |
| 9 | DIY Merchant Service Provider: The Self-Hosted Payment Processor | 257 | 169 |
| 10 | Pfeilstorch: A Novel Approach to Visualizing Network Traffic | 309 | 85 |
1
GoodSystemDesignExplorer
Author
dondraper36
Description
This project is a collection of articles, discussions, and best practices aimed at helping developers understand and implement good system design principles. It tackles the complexities of building scalable, reliable, and maintainable software systems by providing a structured approach to architectural choices and trade-offs. The core innovation lies in curating and presenting this information in a digestible format, making complex system design concepts accessible and actionable for developers of all levels.
Popularity
Points 867
Comments 374
What is this product?
This is a curated resource that explores the fundamentals of good system design. It's not a single tool or a piece of code, but rather a knowledge base. It organizes information on topics like distributed systems, databases, and message queues, offering guidance on how to choose the right technologies and design patterns for your specific needs. The innovation lies in aggregating diverse sources and presenting them in a clear, easily navigable manner, making complex architectural concepts easier to grasp. So, it helps you build better and more robust software.
How to use it?
Developers can use this resource to learn about system design principles and apply them to their projects. The project doesn't require any direct integration with your code. Instead, you read through the curated content – articles, discussions, and guides – and apply the principles to your system design process. For instance, when designing a new microservices architecture, you could consult the resource to understand best practices for inter-service communication. So, you can use it to improve your design skills and build more efficient systems.
Product Core Function
· Understanding Distributed Systems: The resource explains how to design systems that operate across multiple computers, handling issues like data consistency and fault tolerance. This is valuable because it teaches you to create applications that can handle huge amounts of data and traffic without crashing.
· Database Selection and Design: It provides guidance on selecting the appropriate database for your application, whether it's a relational database like PostgreSQL, a NoSQL database like MongoDB, or a specialized database. This helps you make informed decisions to ensure your data storage is efficient, scalable, and matches your application's requirements.
· Message Queues and Asynchronous Communication: The resource covers the use of message queues (like RabbitMQ or Kafka) to enable asynchronous communication between different parts of a system. This is useful for building systems that can handle bursts of traffic and operate reliably even if some components fail.
· API Design and Versioning: The project offers advice on designing APIs that are easy to use, well-documented, and can evolve over time. This means you can create APIs that are easy for other developers (or your future self) to integrate with your application.
Product Usage Case
· Building a Scalable E-commerce Platform: When designing an e-commerce platform that needs to handle thousands of transactions per minute, you can use the resource to understand the trade-offs between different database systems, choose appropriate caching strategies, and design a message queue-based order processing system to handle peak loads effectively. So, you can ensure your e-commerce site can handle large traffic.
· Designing a Real-Time Chat Application: If you are creating a real-time chat application, this resource can guide you on designing a system that can handle a large number of concurrent users, implementing efficient message delivery using techniques like WebSockets, and choosing an appropriate database for storing chat history. So, you can create a fast and reliable chat experience for users.
· Developing a Microservices-Based Application: When building a microservices architecture, you can use the project to understand best practices for inter-service communication, service discovery, and data consistency. This can help you create a system that is modular, scalable, and easy to maintain. So, you can build applications that are easier to update and change.
· Creating a System for Data Processing: You can use the resource to learn about designing data pipelines, selecting appropriate data storage solutions, and implementing fault-tolerant data processing using tools like Apache Kafka or Apache Spark. This helps you build a robust system to handle large datasets. So, you can efficiently process and analyze large volumes of data.
2
ChatControl-Buster: A Privacy-Focused Analysis Tool
Author
givemeethekeys
Description
This project analyzes the impact of EU's 'Chat Control' initiative on user privacy. It leverages technical analysis of the legislation and its implementation, identifying potential loopholes and privacy risks. It doesn't just point out the problem; it delves into the technical mechanisms that make surveillance possible, providing a deep dive into the technologies that could be used to monitor private communications. This offers insights into how to protect user data and enhance privacy, helping users to understand the technical implications of this legislation.
Popularity
Points 422
Comments 341
What is this product?
This project provides a technical breakdown of the EU's 'Chat Control' proposal, explaining the surveillance technologies it enables. It assesses the legal and technical impact on user privacy. It highlights the surveillance technologies and their potential impact. It helps people understand how their communications could be monitored, which is often obscured by legal jargon and technical complexities. So what? This helps you understand the real-world implications of the law, not just the legal wording.
How to use it?
While the project is primarily an analysis of legislation, developers can use the insights to develop privacy-enhancing technologies (PETs). They can learn from the technical vulnerabilities identified in the 'Chat Control' proposal to build tools and systems that better protect user data. This might involve creating more secure messaging applications, building privacy-focused browsers, or developing tools to analyze communication metadata for privacy leaks. So what? By learning about the surveillance technologies, developers can make more private and secure apps and tools.
Product Core Function
· Technical Analysis of Legislation: This function breaks down complex legal text into understandable technical terms, pinpointing key areas of privacy concern within the 'Chat Control' proposal. It simplifies the analysis for non-experts to understand the potential dangers of the law. So what? This helps you understand the law's impact without needing a law degree.
· Vulnerability Assessment: The project identifies potential vulnerabilities in the technical aspects of 'Chat Control'. It examines how existing surveillance technologies could be leveraged, outlining possible scenarios where user data is at risk. So what? This shows you the weak points in the system.
· Privacy Risk Mitigation: The project suggests ways to minimize the risks identified. It provides guidance on how to protect user data from surveillance, which could include recommendations for end-to-end encryption, data minimization practices, or using privacy-focused technologies. So what? This gives you practical tips on how to protect yourself.
· Technical Breakdown of Communication Monitoring: The analysis dissects various methods of communication monitoring, such as scanning for content, metadata analysis, and data retention practices. It explains these technologies and their implications in plain language, making them accessible to a wider audience. So what? This helps you understand how your messages are being watched.
Product Usage Case
· Building Secure Messaging Applications: Developers can incorporate the analysis findings into their messaging apps to ensure user communications are secure and protected from potential surveillance. This might involve using end-to-end encryption, ensuring secure key management, or implementing methods to prevent metadata leakage. So what? You can make apps that are better at keeping secrets.
· Developing Privacy-Focused Browsers: The project provides insights into browser-based tracking technologies and how these could be exploited for surveillance. Developers of privacy-focused browsers can use this information to block or mitigate such tracking attempts, enhancing user privacy. So what? You can use your browser to stay private.
· Creating Audit Tools: Security researchers and developers can use the project’s analysis to build auditing tools. These tools can assess the privacy risks within a system or a software application, helping to identify weaknesses and compliance gaps related to data protection. So what? You can find the holes in a system to better fix them.
· Privacy-Enhancing Technologies (PET) Development: The project’s findings can fuel the development of privacy-enhancing technologies, such as tools for secure storage of sensitive data, anonymization techniques, or applications that allow anonymous communication. So what? You can create new tools that fight surveillance.
3
OpenAI Progress Tracker: A Glimpse into AI Advancements
Author
vinhnx
Description
This project tracks and visualizes the progress made by OpenAI in various AI domains. It's not just a simple data display; it’s about understanding the rapid advancements in AI by monitoring key metrics, research papers, and model performance. It tackles the challenge of staying informed about the fast-paced evolution of AI. So this is useful because it helps you stay updated on the cutting edge of AI research.
Popularity
Points 383
Comments 321
What is this product?
This project gathers and analyzes data related to OpenAI's progress, including new research papers, model releases, and performance benchmarks. It uses web scraping to collect information, natural language processing (NLP) to understand the context of the information, and data visualization techniques to present the insights in an accessible way. This offers a simplified way to digest the complexities of AI developments. So this helps you stay informed about the most recent developments in the field of AI without needing a deep understanding of AI engineering.
How to use it?
While the specifics of how one could 'use' this project directly might not be straightforward since it's a data aggregation and visualization tool, you could use the insights to understand trends, identify key breakthroughs, and assess the impact of AI in different fields. Developers could integrate the data visualizations into their own dashboards or use the data as a foundation for more advanced AI research. For example, someone could use this information to decide which AI areas to focus on or to check the latest advancements in the specific areas they are interested in. So this can be a source of knowledge and inspiration for developers involved in AI or related applications.
Product Core Function
· Data Aggregation: Collects information from various sources, such as research papers, OpenAI blogs, and public datasets. This allows for a consolidated view of OpenAI's progress. So this helps you reduce the time spent on gathering the latest news on AI.
· NLP Analysis: Uses natural language processing to extract key information and understand the meaning behind research papers and announcements. This helps in identifying the significant developments. So this assists you to filter out unimportant information and grasp the essence quickly.
· Performance Metric Tracking: Monitors the performance of OpenAI models across different benchmarks and tasks, such as image generation, text generation, and code generation. This lets you evaluate AI models' practical value. So this helps you to compare AI model's practical capability.
· Trend Visualization: Presents the gathered data through charts and graphs, showing the evolution of AI capabilities over time. This helps to identify trends and visualize the progress. So this can help you visualize how the AI is improving over time in a simplified way.
· Alert System: Provides alerts on significant updates like the release of new models or major advancements in the field. This helps users to stay on top of the latest happenings. So this allows you to keep up-to-date on the most relevant AI news.
Product Usage Case
· AI Research: Researchers use the platform to track the advancements in specific areas of AI, such as natural language processing or computer vision, to compare results with their own work or to better understand the state of the art. This helps researchers stay informed about new research areas or discover new techniques in their projects. So this enables AI researchers to follow industry leaders' progress and identify the latest trends.
· Software Development: Developers can use this platform to follow developments that might influence their projects (e.g., new AI frameworks, models, APIs). This helps developers to find updated AI components and add them to their projects. So this can help developers integrate advanced AI functions into their projects.
· Educational Purposes: Students and educators can leverage the platform to get insights into the field of AI and understand the technical advancements in an accessible and visual way. This can help them gain a clearer understanding of the rapid progress in AI. So this helps educate people who aren't AI experts about the latest developments.
· Investment Decisions: Investors can make informed decisions by using the platform to understand the pace of development and the potential of different AI technologies. This helps in identifying market opportunities and understanding the viability of AI companies. So this provides investors the information to identify promising opportunities in AI.
4
Unscalable Scaling: A Pragmatic Approach to Problem Solving
Author
derwiki
Description
This project, inspired by the philosophy of "doing things that don't scale," focuses on rapidly prototyping and validating ideas before investing in complex, scalable solutions. It encourages developers to prioritize getting something working first, even if the initial implementation is inefficient or manual. The key innovation is the mindset: embrace the non-scalable, understand the core value, and then optimize only when absolutely necessary. It tackles the problem of premature optimization and the paralysis of analysis in software development.
Popularity
Points 488
Comments 202
What is this product?
This is not a specific tool but a philosophical approach to software development. It's about starting simple, often with manual or inefficient processes, to prove a concept or validate a need. It's about focusing on delivering value quickly, even if it means initially building something that won't handle a huge amount of users or data. The innovation lies in reversing the typical development process: prioritize getting it done, then optimize if success warrants it. So, what's the point? It saves time and resources by preventing developers from over-engineering before they know if their idea is even viable.
How to use it?
Developers can use this approach by adopting a "prototype first, scale later" mindset. Instead of immediately building a complex, scalable system, start with a simpler, often manual, solution to test an idea. For example, if you're building a new customer support system, you could initially manage customer inquiries with a spreadsheet and email. Only when you have confirmed that the system is useful and have a clear understanding of how it needs to scale should you then build a more complex, automated solution. This shifts the focus from features to user value, allowing quicker iterations and validation.
Product Core Function
· Rapid Prototyping: Building the minimum viable product (MVP) as quickly as possible, even if it involves inefficient techniques. This allows for quick testing and validation of ideas. So this helps by saving time and money on features that don't provide value.
· User Validation: Focusing on getting early user feedback and testing the core value proposition before optimizing for scale. This validates that your idea is worth developing further. So this ensures that you don't waste effort on projects that people don't need.
· Value-driven Development: Prioritizing delivering value to users over worrying about scalability. This allows you to learn and adapt quickly based on user feedback. So this enables developers to be flexible and adapt to changing demands.
Product Usage Case
· Building a Social Network: Instead of immediately investing in a complex database and infrastructure, start by using a simple forum or email list. Get user feedback, understand what people want, then optimize for scalability if the community grows. So this shows you the value before you invest your time and energy.
· Developing an E-commerce Site: Instead of building an elaborate product catalog with a complex checkout process, start with a single product page and manually process orders. This helps you understand the customer journey before you build the full website. So this makes sure your website is actually user friendly.
· Creating a Customer Relationship Management (CRM) System: Manually track customer interactions in a spreadsheet or a simple database before building a fully-featured CRM platform. This helps to identify the core features needed and understand the workflows. So this saves you the trouble of over-engineering.
5
Keratin Toothpaste - A Bio-engineered Approach to Dental Care
Author
sohkamyung
Description
This project focuses on a novel approach to toothpaste formulation, leveraging the power of keratin, a structural protein found in hair, nails, and teeth. The core innovation lies in incorporating keratin into toothpaste to potentially protect and repair damaged teeth. This tackles the common problem of enamel erosion and damage, offering a potentially more natural and effective solution compared to traditional methods.
Popularity
Points 422
Comments 196
What is this product?
This isn't a software project, but the core concept presents a fascinating use of bio-engineering. The project essentially explores how to use keratin, a protein that's already part of our body's structure, to strengthen and repair teeth. The innovative idea is that keratin could fill in tiny cracks and imperfections in the tooth enamel, offering a natural way to protect against decay and damage. Imagine it as a 'fill-in-the-gaps' approach, unlike the typical abrasive methods of toothpaste.
How to use it?
While the project is a scientific study, if it translates into a consumer product, you'd use it like any other toothpaste: brush your teeth. The key difference would be the potential for your toothpaste to actively repair and protect your teeth, as the keratin interacts with the enamel. This project isn't about a new API or code library; instead, it proposes a tangible solution, demonstrating how biological materials can be integrated into our daily routines to better care for our health.
Product Core Function
· Keratin Incorporation: The central function is the integration of keratin into the toothpaste formula. This is the core technology. It’s valuable because it introduces a natural biomaterial to potentially enhance the teeth's protective layer. So this allows for potential enhanced protection against external threats like acids from foods and drinks.
· Enamel Repair: If the keratin can integrate into the tooth's structure, the project could potentially mend micro-cracks and strengthen the enamel. So this addresses a crucial problem: enamel degradation, which leads to cavities and sensitivity.
· Bio-Compatibility: Keratin is naturally present in our bodies. It is very helpful because it reduces the chances of any allergic reactions or adverse impacts, so using a natural substance increases the safety factor of toothpaste.
· Potential for Enhanced Tooth Health: The ultimate goal is to use keratin to better your teeth's health in a more biological and natural manner. So it can improve teeth overall, leading to better oral health.
Product Usage Case
· Preventative Care for Tooth Sensitivity: People with sensitive teeth often struggle with everyday foods and drinks. If keratin toothpaste can repair and rebuild enamel, this could significantly reduce or eliminate their sensitivity. So this helps many people with existing dental problems and also prevent future ones.
· Repair of Micro-Cracks: Our teeth get tiny cracks from daily use. Keratin toothpaste can then effectively heal those cracks. So people can maintain strong teeth and can avoid cavities and other dental problems.
· Enhanced Protection for Enamel Erosion: For individuals who consume acidic food and drinks, toothpaste like this provides extra protection. So it can prevent the enamel from eroding, protecting teeth from damage.
6
Horsepower Unlocker: A Software-Defined Performance Booster
Author
t0bia_s
Description
This project explores the controversial practice of Volkswagen locking horsepower behind a paid subscription. It's a technical dissection of how car manufacturers are utilizing software to control vehicle performance and monetize features. The project likely involves reverse engineering and identifying the software mechanisms responsible for limiting horsepower, potentially leading to the ability to 'unlock' this performance. It addresses the growing trend of software-defined features and the ethical implications of restricting performance that is already built into the car.
Popularity
Points 176
Comments 304
What is this product?
This project likely involves analyzing the software in Volkswagen cars to understand how they control horsepower through subscriptions. Imagine your car has more power 'hidden' inside, but you need to pay to access it. The project attempts to understand and potentially bypass these software locks, offering insight into how car companies are managing features through software, and questioning ownership of these hidden capabilities. The innovation lies in understanding the software's logic and exploiting any vulnerabilities.
How to use it?
This project is primarily relevant to automotive enthusiasts and researchers. Developers could use the project's findings to understand how in-car software operates, analyze the communication protocols used, and potentially create their own tools for car diagnostics or performance tuning. It could be used to understand the software behind paid features. For example, you might use it to understand how a specific performance upgrade is activated and deactivate the software lock. The project provides technical insights that can be applied to reverse engineering and understanding automotive software.
Product Core Function
· Reverse Engineering of Car Software: The core function likely involves examining the car's software to identify the code that limits horsepower. The value is in understanding the internal workings of the car's systems, which can be applied to diagnose problems or customize car performance. So this can help understand how software controls performance, opening the door for modifications.
· Communication Protocol Analysis: Identifying the communication methods used between the car's various electronic control units (ECUs) and the central computer. The value is in learning how the car's components talk to each other and understanding how the car's software interacts with its hardware. So it gives you tools to 'talk' to your car.
· Exploiting Software Vulnerabilities: Identifying any security flaws or weaknesses in the software that allow unauthorized access to the horsepower control. The value is in understanding how software can be manipulated and how to protect it from manipulation. So it helps to find out if the car's computer can be tricked into doing things it shouldn't be doing.
· Performance Unlocking Mechanism: Potentially creating a method to bypass or modify the software restrictions, thereby unlocking the car's full horsepower. The value is in understanding how to modify car performance and giving users greater control over the vehicle's capabilities. So it gives you the ability to bypass the software locks and access the hidden horsepower.
Product Usage Case
· Automotive Enthusiasts Customization: A car enthusiast who wants to customize their Volkswagen car to run at peak performance. They can use the project's findings to understand the software locks in place. So it helps to better understand and modify the car's control software.
· Security Researchers Analysis: Security researchers who are interested in analyzing the car's software security vulnerabilities and how such software can be exploited. The project's findings can be used to inform security protocols and develop more secure car systems. So it enables the evaluation of potential security risks.
· DIY Diagnostic Tools: An experienced developer wants to create custom diagnostic tools for Volkswagen cars. The project can be used to understand the communication protocols and data formats used by the car's ECUs. So it provides the information needed to build tools for diagnostics and troubleshooting.
· Ethical Considerations and Consumer Advocacy: The project might bring to the forefront the discussion around the ethics of locking horsepower behind a paywall. By understanding the technical aspects, consumers and advocacy groups can better address the issues of car manufacturers controlling features already present in the car. So it facilitates the conversation about what we really own when we buy a car.
7
OnionSlice: Optimal Onion Dicing with Computational Geometry
Author
surprisetalk
Description
OnionSlice is a project that tackles the seemingly simple problem of dicing an onion, but approaches it with mathematical rigor. It uses computational geometry to determine the most efficient and uniform way to cut an onion into perfect cubes. This project showcases how complex mathematical concepts can be applied to solve everyday problems, providing a practical application of theoretical knowledge. It aims to minimize the number of cuts while ensuring all onion pieces are of equal size. So this is useful for anyone wanting to minimize effort and maximize efficiency in the kitchen, or anyone interested in applied mathematics.
Popularity
Points 341
Comments 130
What is this product?
OnionSlice employs algorithms from computational geometry – essentially, the mathematics of shapes and space – to figure out the best way to cut an onion. It considers the onion's shape and calculates the optimal slice angles and positions. The innovation lies in applying these advanced mathematical principles to a culinary task, ensuring uniform and efficient dicing. So this is an innovative approach to a common problem, providing a precise and efficient solution.
How to use it?
While the project's core might be mathematical, the principles could be applied in a few ways. Imagine using a robotic arm controlled by this algorithm in a food processing factory, leading to more uniform and efficient onion processing. For developers, the project can be a learning tool to understand how to apply mathematical concepts to practical problems and an inspiration to integrate geometry algorithms into their code for tasks that require precision or optimization. You can adapt the core concepts in areas like 3D modeling or precise cutting tasks. So this can give you an innovative edge in various development tasks.
Product Core Function
· Optimal Slice Calculation: Determines the precise angles and positions for each cut to create uniformly sized onion cubes. This is achieved using algorithms from computational geometry. Applications could include automated cutting in food processing factories, or precision cutting tasks.
· Volume Optimization: Aims to minimize the number of cuts required while maintaining uniform piece sizes. This leads to greater efficiency and reduced waste. This optimizes processing time and reduces material waste in any cutting task.
· Shape-Aware Algorithm: Adapts to the specific shape of the onion to provide the best cutting strategy. This ensures the final pieces are close to uniform, regardless of the onion’s original size or form. Adaptability allows the system to be used on irregularly shaped materials.
Product Usage Case
· Automated Food Processing: Imagine a food processing plant using this to automate the dicing of onions. Robots could use the calculated angles to perform fast, precise cuts, boosting efficiency and consistency in the final product. This ensures uniform product quality in mass production.
· 3D Modeling & Fabrication: The geometrical principles can be applied to creating 3D models for cutting and fabrication. For example, it can be adapted to provide precise cutting instructions for materials where precision and minimizing waste are key. This streamlines prototyping and manufacturing processes.
· Educational Tool: Developers could use this as a learning tool to understand how geometric algorithms work and explore their applications in unexpected domains, such as food preparation. This helps developers to connect theoretical concepts with practical applications.
8
IONIQ 5 Patch Payment Analysis Tool
Author
duxup
Description
This project analyzes the Hyundai IONIQ 5's cybersecurity patch payment requirement. It focuses on understanding the technical implications of charging customers for security updates, examining the patch's architecture and the business model implications. The innovation lies in its approach to dissecting a controversial technical decision by a major car manufacturer, highlighting the intersection of software, security, and consumer rights.
Popularity
Points 243
Comments 198
What is this product?
This isn't a software tool itself but an analysis of Hyundai's decision to charge IONIQ 5 owners for a cybersecurity patch. It digs into the technical aspects. The core of this project would analyze the patch itself (hypothetically), examining how it fixes vulnerabilities and how its delivery mechanism works. It would assess the costs involved, the security risks without the patch, and the implications of paywalls on critical security updates. Innovation comes from critically examining a real-world technical policy in the automotive industry.
How to use it?
Developers wouldn't directly 'use' this project as a piece of code in their applications. Instead, they'd be inspired by its critical thinking approach. Developers could study the project's methodology – how it breaks down a complex technical issue into manageable parts, researching, and assessing the impact of software changes on users. For instance, developers can create tools to analyze security patches of any software. It's about applying a critical security mindset. So, how can you use it? If you're a security-focused developer, you can learn about supply chain vulnerabilities.
Product Core Function
· Vulnerability Analysis: This involves identifying the specific security flaws addressed by the patch. It's about understanding 'what' the patch fixes and 'how' it protects the vehicle's systems. The value lies in knowing the scope of the security threats and preventing malicious activities. For example, it helps to understand a certain vehicle model might have security vulnerabilities, and thus, it's useful to know the patch is necessary for it.
· Patch Delivery Mechanism Examination: Analyzing how the patch is distributed (over-the-air, dealership, etc.). This assesses the efficiency and accessibility of the update process. This helps developers to implement better software updating features that make it easy for users. So, developers can use the insight to see how an important feature can be effectively delivered.
· Cost-Benefit Analysis of the Patch: This involves evaluating the financial implications of providing a security patch for free or charging for it. It's about understanding the business model around cybersecurity, which affects the customer's satisfaction. This information enables us to consider the ethical and economical implications of security patches. It also enables us to improve the quality of service. So, this can make a business model successful.
· Assessment of Customer Impact: This involves analyzing how the charging for a cybersecurity patch could affect the vehicle owners. This helps developers to develop better software updating features that make it easy for users. Thus, we can improve user experience and avoid the customers to pay for the critical security update.
Product Usage Case
· Analyzing Tesla's Over-the-Air Updates: Developers could apply the same principles to analyze how Tesla delivers its updates. By examining the update process, they can identify potential vulnerabilities in its update system and assess its security measures. This helps improve the security of software updating in other areas.
· Analyzing the Impact of Firmware Updates for IoT Devices: Understanding the security and the cost of updates can help analyze the broader security implications of IoT devices. By studying this, developers can understand how this impacts the security of devices, user privacy, and business operations. This can help identify better methods to protect the system from malicious activities.
9
DIY Merchant Service Provider: The Self-Hosted Payment Processor
Author
progval
Description
This project details the creation of a self-hosted merchant service provider, essentially a way to process online payments without relying on third-party services. The innovation lies in demonstrating how to bypass traditional payment gateways, giving developers more control over the payment infrastructure and potentially reducing costs. It tackles the problem of vendor lock-in and high fees associated with established payment processors.
Popularity
Points 257
Comments 169
What is this product?
This project is about building your own payment processing system. Instead of using companies like Stripe or PayPal, you're learning how to handle payment transactions directly. It involves understanding the technical intricacies of payment processing, like secure communication with banks and managing transactions. The innovation lies in empowering developers to control their payment infrastructure, which can lead to lower costs, more customization, and a deeper understanding of how payments work. So this means you have more control over your money.
How to use it?
Developers can use this project as a learning tool or as a basis for building their own custom payment solutions. You'd need to understand how payment APIs work (like those provided by banks) and how to securely handle sensitive financial data. You could integrate this into an e-commerce platform, a subscription service, or any application that requires online payments. It allows you to tailor the payment process to your exact needs. So you can customize your payment process to fit your business, rather than adapting to a pre-built system.
Product Core Function
· Payment Gateway Integration: This involves the core technical steps of communicating with different financial institutions and payment networks (e.g., Visa, Mastercard). The project demonstrates how to build the communication protocols needed to send payment requests and receive transaction confirmations. This allows you to process various payment methods, giving you control over supported payment types. So this allows you to accept payments from different sources.
· Security and Compliance (PCI DSS): Handling financial data securely is crucial. The project likely includes guidance on encrypting data, using secure protocols (like HTTPS), and adhering to PCI DSS (Payment Card Industry Data Security Standard) compliance, which is a set of security standards for handling cardholder data. This ensures the safety of user data, avoiding potential legal issues and building user trust. So this protects your customers' payment information.
· Transaction Management: This involves building the logic to manage different transaction states (pending, successful, failed), handling refunds, and generating reports. This provides a complete picture of the payment activity, giving you the tools to reconcile accounts and identify fraud. So this gives you the ability to track and manage all your transactions.
· Risk Management and Fraud Prevention: This section typically includes techniques to detect and prevent fraudulent transactions, such as implementing fraud detection algorithms, checking for suspicious patterns, and implementing security rules. This protects your business from financial losses and chargebacks. So this allows you to avoid financial losses due to fraudulent transactions.
Product Usage Case
· Custom E-commerce Platform: A developer builds an online store for niche products and wants to avoid the fees and limitations of existing payment processors. They implement this self-hosted system to directly handle payments, offering custom payment flows, lower fees, and full control over the customer experience. So you can build a store to sell your product in your own way, no matter what the payment service provider is.
· Subscription-Based Service: A developer builds a platform that sells subscriptions. Implementing this allows the developer to manage recurring payments directly, offering flexible pricing options, and integrating with their existing user management system. So you can manage the recurring payments yourself to fully control the pricing and offer your customer the right service at the right time.
· High-Volume Sales Applications: A company processes a large number of transactions. Building a self-hosted payment system allows them to optimize the payment process for performance, reduce costs, and integrate payment processing seamlessly with their business systems. So if you sell a lot of products, you can optimize your payment process.
10
Pfeilstorch: A Novel Approach to Visualizing Network Traffic
Author
gyomu
Description
Pfeilstorch is a project aiming to visualize network traffic in a unique and insightful way. It likely uses a combination of data collection, parsing, and presentation techniques to provide developers with a clearer understanding of network activity, helping them identify bottlenecks, security issues, and overall network performance. The core innovation lies in its visualization methodology, potentially using novel graphical representations to overcome the limitations of traditional network monitoring tools.
Popularity
Points 309
Comments 85
What is this product?
Pfeilstorch is essentially a tool that helps you 'see' what's happening on your network. Instead of just showing numbers and statistics, it likely translates the complex data of network traffic into visual representations, making it easier to understand. This allows developers to quickly identify issues such as slow loading times, unauthorized access attempts, or excessive data usage. It likely achieves this by capturing network packets, analyzing them, and then presenting the data in an easy-to-understand graphical format. So it helps you quickly understand how your network is performing and diagnose problems.
How to use it?
Developers would likely use Pfeilstorch by running it on a machine connected to their network. It would passively monitor the network traffic, and generate a real-time visualization. This could be accessed through a web interface or a dedicated application. To integrate it, developers would likely point the tool to the relevant network interface. This is very useful for identifying problems or security concerns. So you can see what’s happening on your network, how your traffic flows, and pinpoint issues quickly.
Product Core Function
· Real-time Network Traffic Monitoring: This allows developers to see the activity on their network as it happens. The real-time monitoring allows developers to respond to performance issues or security threats without delay. So you get immediate insights into network activity.
· Data Packet Analysis: The tool breaks down network traffic into its constituent parts. This provides a deeper understanding of what types of data are being transmitted and received. This helps pinpoint bandwidth-hogging applications or potential security vulnerabilities. So you can understand the 'ingredients' of your network traffic.
· Novel Visualization Techniques: Pfeilstorch uses innovative ways to present the data, moving beyond basic charts and graphs. This allows developers to quickly grasp the overall network health, identify unusual patterns, and understand complex relationships between devices and services. So you can get a clearer picture of what’s happening on your network.
· Customizable Alerts: Developers can configure alerts for specific events, such as unusual traffic patterns or security breaches. This enables proactive network management and swift responses to potential issues. So you can be notified of problems as soon as they arise.
Product Usage Case
· Debugging Performance Issues: A web developer notices their website is loading slowly. By using Pfeilstorch, they can quickly identify that a large amount of data is being transferred from a particular server, allowing them to optimize their website's content delivery network (CDN). So it helps identify and fix slow-loading websites.
· Security Threat Detection: A security engineer uses Pfeilstorch to monitor network traffic for suspicious activity. They notice unusual patterns of data transfer from a specific device, indicating a potential security breach. This allows the engineer to quickly investigate and mitigate the threat. So it helps find and stop security breaches.
· Network Optimization: A system administrator uses Pfeilstorch to analyze network traffic and identify bottlenecks. They discover that a particular application is consuming a disproportionate amount of bandwidth. This allows them to optimize the network configuration to improve overall performance. So it helps optimize your network to work at its best.
· Monitoring IoT Devices: An embedded systems engineer can monitor traffic from IoT devices to observe their communication patterns. This can help detect communication anomalies that might point towards device compromise or malfunction. So it helps keep IoT devices secure and functioning.
11
Windows Bloatware Remover (WBR)
Author
rntn
Description
This project aims to tackle the growing problem of bloatware in Windows. It's essentially a script that automates the process of removing unwanted pre-installed applications and features. The innovation lies in its approach to identifying and safely removing these components, preventing the common issues that arise from incorrect removal. It provides a safer and more efficient way to customize the Windows experience for users who want a cleaner and more streamlined system, addressing the pain points of performance degradation and unwanted resource consumption.
Popularity
Points 183
Comments 198
What is this product?
WBR is a script, possibly using PowerShell or a similar scripting language, designed to uninstall or disable specific Windows features and pre-installed applications. The core innovation is likely in its curated list of bloatware targets, the method of removing them safely (avoiding breaking the OS), and potentially the user-friendly interface or automation to simplify the process. It’s built to give users control over their operating system, rather than having their system dictate what apps are installed.
How to use it?
Developers can use WBR by running the script within a Windows environment, likely through a command-line interface or a graphical user interface (GUI). It would involve selecting the bloatware to remove or disable and then executing the script. This tool can be used to create custom Windows installations, enhance the performance of existing systems by removing resource-intensive apps, or simply to declutter the user experience. For example, it could be incorporated into system imaging processes or deployment scripts.
Product Core Function
· Identifying Bloatware: The script likely contains a database or a list of known bloatware applications and features pre-installed on Windows. This allows the script to target and remove them. So what? This saves you the time and effort of manually identifying unwanted software.
· Safe Removal Mechanisms: WBR likely uses robust methods for uninstalling or disabling software without destabilizing the operating system, such as using PowerShell cmdlets or built-in Windows tools. It might also implement safeguards like creating system restore points before making changes. So what? You get a cleaner system without risking your data or the stability of your OS.
· User-Friendly Interface (Potentially): The project may offer a command-line interface (CLI) or a GUI, making it easier for users to select which components to remove. This could include checkboxes or menus to guide the user. So what? This makes it easier for even non-technical users to clean their Windows installations.
· Configuration Options: The script might allow users to customize the removal process, such as choosing between uninstalling and disabling applications, or including/excluding certain components. So what? This provides flexibility, allowing you to tailor the tool to your specific needs and preferences.
Product Usage Case
· Clean Windows Installation: A developer can use WBR to create a custom Windows installation image, removing unnecessary software before deployment to devices. This reduces the initial system load, making the operating system faster and more responsive from the start. So what? Your newly installed Windows runs smoother, faster.
· Performance Optimization: If you're a developer who is working with a Windows machine that's running slow, you can use WBR to uninstall resource-intensive pre-installed apps, such as unnecessary games or background services, freeing up system resources and improving overall performance. So what? This means your development environment is faster, leading to improved productivity.
· Privacy Enhancement: Some bloatware might collect usage data. By removing this software, you reduce the amount of data that is sent from your computer. So what? This gives you more control over your data and increases your privacy.
· Virtual Machine Customization: Developers building virtual machine images can use WBR to create leaner and more efficient virtual environments. So what? Reduces resource consumption of VMs, allowing you to run more of them concurrently.
12
Developer Traps Detector
Author
qouteall
Description
This project aims to identify common pitfalls and anti-patterns in software development, offering a tool to automatically detect and warn developers about potential issues in their code, like resource leaks or inefficient algorithms. It achieves this through static analysis and pattern recognition, making code review more efficient and helping developers avoid costly mistakes.
Popularity
Points 246
Comments 104
What is this product?
This is a tool that scans your code and looks for common mistakes or 'traps' that developers often fall into. It works by analyzing your code without actually running it. It identifies potential problems like memory leaks (where your program forgets to release memory, slowing it down), inefficient loops (where the code takes longer than necessary to complete a task), or security vulnerabilities. So, it's like having an extra set of eyes to catch potential problems early on.
How to use it?
Developers would integrate this tool into their build process, likely as a command-line tool or a plugin for their code editor. They would run the tool on their codebase before committing changes. The tool would then provide a list of potential issues, pinpointing the location in the code where the problem exists and offering suggestions for improvement. This allows developers to catch and fix errors early, saving time and effort in the long run.
Product Core Function
· Static Analysis: The core function is to statically analyze source code. It examines the code's structure and patterns without executing it. This is valuable because it allows the tool to quickly identify potential problems without the need for extensive testing or debugging.
· Anti-Pattern Detection: Identifying common 'anti-patterns' (bad coding practices). For example, detecting redundant code, overly complex functions, or misuse of certain libraries. This is important for improving code readability, maintainability, and reducing the likelihood of future bugs.
· Vulnerability Scanning: The tool scans for potential security vulnerabilities, such as insecure code or the use of outdated libraries with known security flaws. This feature is crucial for ensuring the application's security and protecting against potential attacks.
· Performance Bottleneck Identification: Identifying parts of the code that may be slow or inefficient. This might involve detecting loops that are not optimized or resource-intensive operations. This helps developers optimize their code for better performance.
Product Usage Case
· Identifying Memory Leaks: Imagine a developer using a large library that is not always properly releasing memory. This tool can identify where this memory is being allocated but not deallocated, allowing the developer to fix the issue and prevent the program from slowing down over time. This prevents the software from crashing and improves user experience.
· Detecting Inefficient Loops: A developer writes a loop that iterates through a large dataset, but the code could be optimized to run much faster. The tool identifies this performance bottleneck and suggests using a more efficient algorithm. This results in faster execution times and a better user experience.
· Highlighting Security Vulnerabilities: A developer uses an outdated version of a library with known security flaws. The tool flags the use of this vulnerable library and suggests upgrading to a secure version. This improves the application’s security posture and protects against potential attacks.
· Suggesting Code Style Improvements: The tool can also identify areas where code doesn't follow the project's style guidelines (e.g., inconsistent indentation or naming conventions). This helps developers write more readable and maintainable code. This makes the code easier to understand and work with, which reduces the risk of future errors.
13
Dev Compass: Programming Philosophy Quiz
Author
todsacerdoti
Description
Dev Compass is a quiz designed to help developers understand their programming philosophy. It does this by asking a series of questions, analyzing the answers, and then suggesting which programming philosophies best align with the developer's preferences and approaches. The technical innovation lies in the sophisticated logic used to categorize responses and map them to different philosophical frameworks, effectively creating a personalized roadmap for developers seeking to improve their skills and understanding of code. It solves the problem of self-discovery within a complex and often abstract field like software development.
Popularity
Points 204
Comments 100
What is this product?
Dev Compass is essentially a personality quiz for developers. It works by posing thought-provoking questions about your coding habits, preferences, and beliefs. Behind the scenes, it uses a carefully crafted system to interpret your answers. The system maps your responses to different programming philosophies, like object-oriented programming, functional programming, or even less common approaches. It then provides you with a profile that highlights which philosophies best suit your style. So, instead of just guessing, it gives you data-driven insights into your coding approach.
How to use it?
Developers can access the quiz through a web interface (assuming it's a web app) and answer the questions. After completing the quiz, they'll receive a personalized report. This report will suggest programming philosophies that resonate with their style and offer resources for further learning. Developers can use this to identify areas for growth, discover new coding paradigms, and better understand their strengths and weaknesses. You can use this as a starting point for learning a new programming paradigm.
Product Core Function
· Questionnaire and Answer Collection: The core of the project lies in the well-designed questions that aim to extract a developer's preferences and approaches. The value here is in the ability to accurately capture the nuances of how a developer thinks, and the application is in providing a reliable baseline for analysis.
· Response Analysis Engine: This is where the magic happens. The engine is designed to analyze the quiz answers, identifying patterns and correlations. The value lies in the sophisticated logic that translates raw data into meaningful insights. You get a personalized understanding of their coding style, leading to more informed learning.
· Philosophy Mapping: The engine maps the analyzed responses to various programming philosophies, such as object-oriented, functional, or reactive programming. This capability allows users to understand their current coding philosophy. So that you can discover the next paradigm for your next project.
· Personalized Recommendation: The system offers a personalized report that identifies the programming philosophies that align with the developer's responses. The value here is in providing developers with a custom-tailored roadmap for skill development. You can find learning resources and focus on areas for growth.
· Reporting and Visualization: The project presents the analysis results in a clear and understandable format, likely with a detailed report that provides recommendations and insights. This ensures the results are not just technical jargon but provide valuable action items for the developer. This helps in grasping the implications of your coding preferences.
Product Usage Case
· Beginner Developers: A beginner can use this quiz to explore different coding philosophies before committing to a specific approach. So they can start their journey in the best manner, tailored to their understanding.
· Experienced Developers: Developers already in the field can use the quiz to reflect on their coding style and find blind spots. You can optimize existing code by integrating new insights and paradigms that align with their preferences.
· Team Leaders: Team leaders can leverage this tool to identify and leverage the individual strengths within the team. You can optimize team composition, fostering a more collaborative and effective development environment.
· Self-Improvement Tool: This project can be an excellent tool for a developer seeking personal improvement and a deeper understanding of their own coding practices. So that you can focus on your strengths and improve the areas that need attention. You can learn new techniques that fit with your style.
14
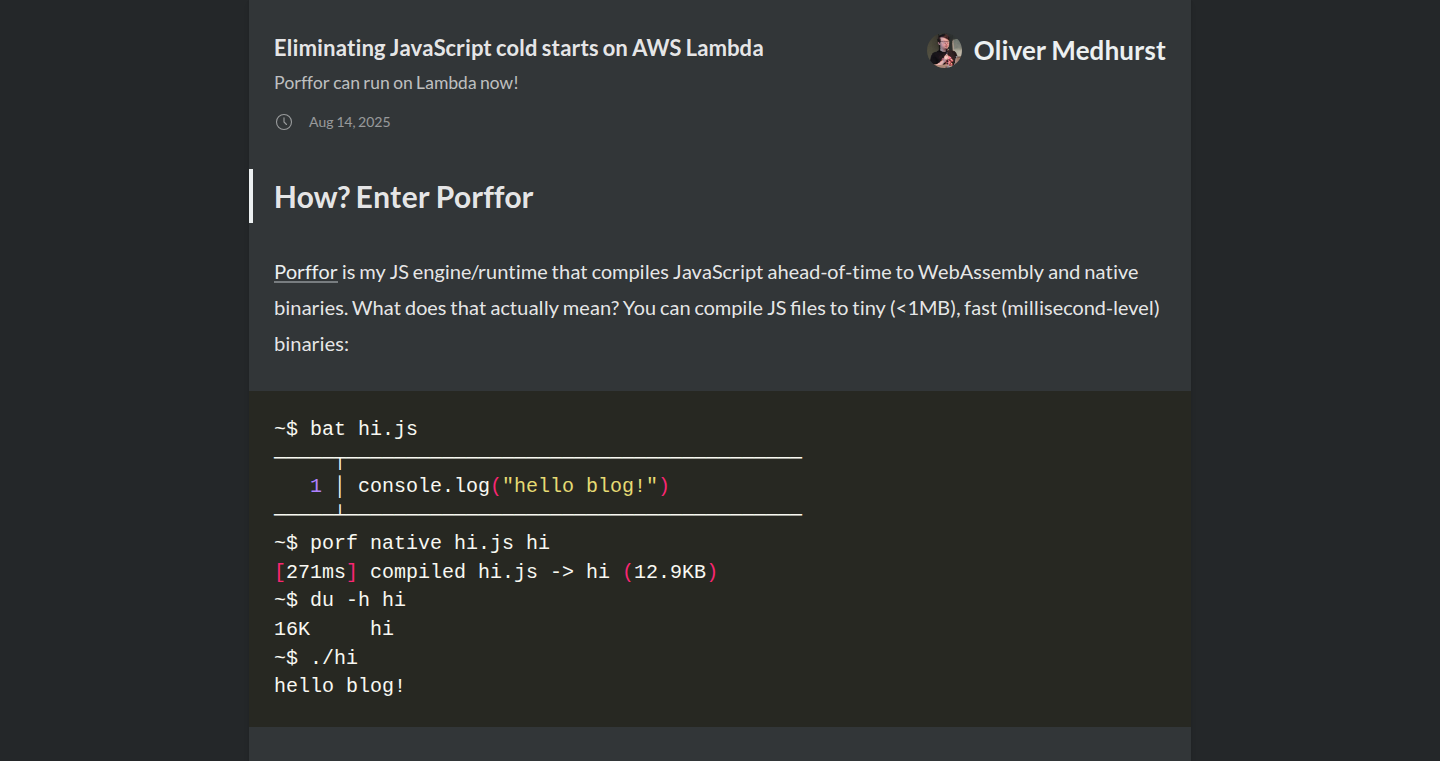
LambdaWarmup: JavaScript Cold Start Killer
Author
styfle
Description
LambdaWarmup tackles the dreaded cold start problem in serverless JavaScript functions running on AWS Lambda. It introduces a clever mechanism to keep your functions 'warm' by proactively invoking them in the background, ensuring quick responses when real user requests arrive. This eliminates the delay users experience when a function needs to 'wake up' for the first time, improving performance and user experience.
Popularity
Points 183
Comments 68
What is this product?
LambdaWarmup is essentially a smart scheduler for your serverless functions. It monitors your AWS Lambda functions and automatically triggers them at regular intervals. This keeps the function code ready to execute, so when a user sends a request, the function responds almost instantly. The innovation lies in its simplicity and effectiveness in mitigating cold start latency, a common pain point for developers using serverless architectures.
How to use it?
Developers integrate LambdaWarmup by deploying it as a separate function or service within their AWS environment. They configure it to monitor their other Lambda functions and set the desired warmup frequency. It integrates with the AWS API and requires basic permissions to invoke and manage other Lambda functions. So you can have a function that invokes your actual logic and keeps it always ready.
Product Core Function
· Background Invocation: LambdaWarmup periodically calls your Lambda functions in the background. This keeps the function's execution environment active and ready to handle requests. So this means faster response times for your users, which is a big deal for any web application.
· Monitoring & Scheduling: The tool monitors function invocation metrics and intelligently schedules warmups based on traffic patterns and performance data. This is like having a smart assistant optimizing your function's availability. So you get better performance without having to constantly babysit the functions yourself.
· Customization: Users can configure the warmup frequency, invocation payloads, and other parameters to fine-tune the behavior for their specific needs. It lets you tailor the warming process to your specific application. This allows you to maximize performance and minimize resource usage based on your app's traffic.
· Automated Management: LambdaWarmup automates the often-manual process of warming up serverless functions. It reduces the need for developers to write their own custom scripts or use complex orchestration tools. So, you spend less time on infrastructure management and more time building awesome features.
Product Usage Case
· E-commerce Website: An e-commerce platform uses LambdaWarmup to keep its product search function warm. This ensures that users can quickly search for items without delays, even during peak traffic periods, leading to a better shopping experience and preventing user abandonment. So faster search means more sales.
· API Gateway: A REST API built on AWS Lambda uses LambdaWarmup to keep its critical API endpoints warm. This results in consistently low latency for API requests, improving the responsiveness of mobile apps and web applications that consume the API. So API calls feel snappy and responsive to users.
· Real-time Applications: A real-time chat application leverages LambdaWarmup to keep its message processing functions warm. This prevents delays in message delivery, ensuring a smooth, responsive user experience in the chat interface. So, users get their messages instantly.
· Serverless Backends: Developers building serverless backends for various applications use LambdaWarmup to reduce latency of critical functions like database queries and authentication processes. This provides a more robust and performant user experience across the board. So you get faster logins and data retrieval.
15
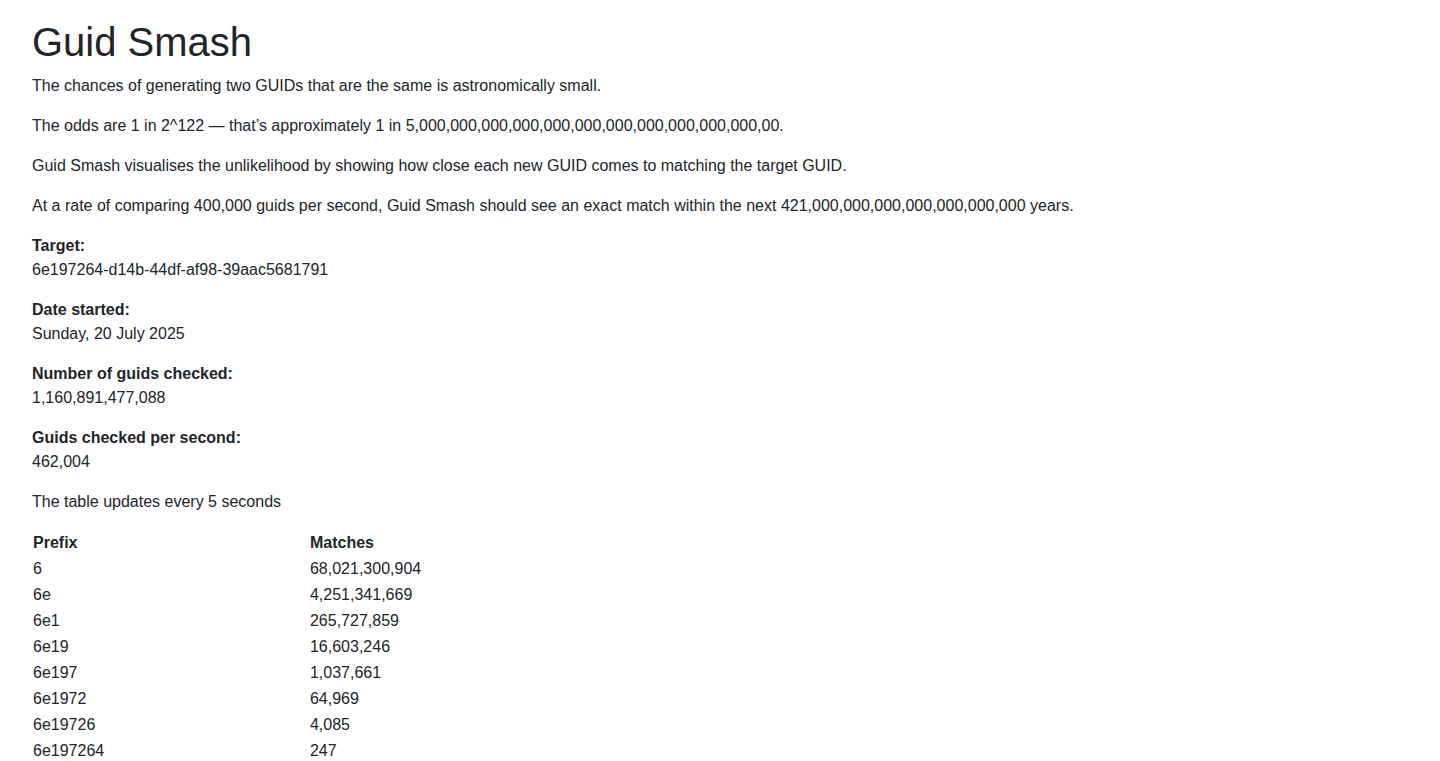
Guid Smash: Effortlessly Extract and Optimize GUIDs
Author
nugzbunny
Description
Guid Smash is a tool designed to efficiently extract and analyze Globally Unique Identifiers (GUIDs) from various text sources. It tackles the common problem of dealing with GUIDs in data, code, or logs, offering rapid identification and validation of these unique identifiers. The core innovation lies in its streamlined parsing algorithms and user-friendly interface, making GUID handling less cumbersome and more accessible.
Popularity
Points 175
Comments 67
What is this product?
Guid Smash is a specialized utility that quickly identifies and extracts GUIDs from text. Think of it as a smart search-and-find tool, but specifically for these long, complex strings that are used to uniquely identify things. It’s innovative because it is optimized for this specific task. So what? This means you can quickly sift through data and find what you need without having to manually hunt for GUIDs. It validates GUIDs and offers basic statistical insights such as identifying the number of unique GUIDs found. Therefore it is designed to simplify the process of handling and managing GUIDs.
How to use it?
Developers can use Guid Smash by simply providing text input, like a code file, log data, or any other text containing GUIDs. The tool then scans the input and outputs a list of extracted GUIDs. It can be integrated into scripts or automated processes, such as checking for GUID consistency in a codebase or quickly identifying records with specific identifiers in a database. So what? This lets developers automate tasks, ensure data integrity, and save time when working with applications and systems that use GUIDs.
Product Core Function
· GUID Extraction: This is the primary function, efficiently locating and extracting GUIDs from raw text input. Technical value: The speed and accuracy of extraction are crucial for large datasets and high-volume processing. Application: Used to quickly parse through massive log files to extract event identifiers for troubleshooting.
· GUID Validation: This function verifies the format of each extracted GUID, ensuring it adheres to the standard specifications. Technical value: This ensures data integrity and prevents errors caused by incorrectly formatted GUIDs. Application: This is used to automatically validate GUIDs in configuration files before deployment.
· Duplicate Detection: Identifies and reports duplicate GUIDs within the input text. Technical value: Helpful for spotting data inconsistencies and potential issues within a system. Application: This is used to identify potential data corruption or conflicts in databases or distributed systems.
· Summary Statistics: Provides basic statistics like the total number of GUIDs found, the number of unique GUIDs, and perhaps a count of duplicates. Technical value: Offers a quick overview of the GUID landscape within a given dataset. Application: Used to rapidly assess the scope of a data migration or integration project.
Product Usage Case
· Log Analysis: A developer is troubleshooting a distributed system and needs to identify all events associated with a specific GUID. Guid Smash quickly extracts all matching GUIDs from the system’s log files. So what? This greatly reduces the time and effort required to pinpoint and resolve issues in complex systems.
· Code Review: A software engineer is reviewing code and wants to ensure all GUIDs are valid. Guid Smash validates all GUIDs within the codebase, highlighting any format errors. So what? This helps maintain code quality and prevents potential runtime errors.
· Data Migration: During a database migration, a team uses Guid Smash to ensure that all GUIDs in the source data are unique and correctly formatted before moving to the new database. So what? This helps ensure the data consistency during migration and prevents data conflicts.
16
LinkKeeper: The Decentralized Memory for Your Digital Life
Author
indus
Description
LinkKeeper is a conceptual project born from the observation that many bookmarking services, once promising, have either disappeared or shifted their focus away from user needs. It's an exploration of how we might build a bookmarking system that is resilient, user-centric, and integrates with the current AI landscape. It's not just about saving links; it's about remembering and revisiting the digital information that matters most. The core technical innovation lies in thinking about a decentralized, AI-enhanced bookmarking system, avoiding the pitfalls of centralized platforms and emphasizing user control and data accessibility. It doesn't provide a working application, but more a set of ideas and a direction.
Popularity
Points 69
Comments 116
What is this product?
LinkKeeper imagines a bookmarking system designed around user autonomy and lasting value. It tackles the core problem of disappearing bookmarking services by proposing a system that’s resistant to the 'make more money' cycle that often leads to product decline. The core idea is to use decentralized storage or a similar system to ensure that your bookmarks don’t vanish if the service provider does. Integration with AI is also considered, potentially using AI to enhance bookmark retrieval, summarization, and even surfacing relevant content based on your saved links. So this means that your links, notes and thoughts will be preserved and easily found even years later.
How to use it?
LinkKeeper is currently a conceptual project, so there isn't a ready-to-use application. However, if a similar system were to exist, developers could integrate with it through APIs to save, organize, and retrieve bookmarks. This integration would empower users to build applications that leverage their stored information. Developers could use it in writing apps, learning apps, or even building data collection tools. So you could build a customized way of saving and recalling any link you read!
Product Core Function
· Decentralized Storage: Instead of relying on a single server, LinkKeeper considers storing bookmarks across multiple locations. This ensures that the data remains accessible even if one server goes down or the service is no longer maintained. So, no single point of failure, your bookmarks are always safe.
· AI-Enhanced Retrieval: LinkKeeper imagines integrating AI to assist with bookmark organization, search, and recommendations. AI could summarize pages, categorize bookmarks, and suggest related content. So, finding the perfect page is always easy, even with hundreds of links.
· User-Centric Design: LinkKeeper's design will prioritize user experience and control. Features like easy tagging, search, and customization will be essential. The goal is to give users complete control over their data and how they interact with it. So, you get to tailor the system to your needs, not the other way around.
· Open Standards and APIs: The project would ideally be built on open standards, allowing other developers to build on top of the platform. This could include APIs for bookmarking, retrieving data, and integrating with other tools. So, developers can add this to their apps and save the data.
Product Usage Case
· Personal Knowledge Management: A student can save research links, tag them by topic, and use AI to summarize key takeaways, helping with study and essay writing. So, you can build a knowledge base around the things that interest you.
· Professional Research: A professional could bookmark relevant articles, analyze industry trends, and use AI to generate reports. So, keep track of the best content and have it organized when you need it.
· Content Curation: A content creator can curate links and resources for articles, blog posts, and social media. AI can help identify relevant links for content creation. So, you can build content faster by using the right links when creating it.
17
ProcessorTraceAnalyzer: A Deep Dive into Apple Silicon's Inner Workings
Author
xdevweeknds
Description
This project analyzes Apple's Processor Trace instrument, a powerful tool that allows developers to peek inside the CPU and understand how their code is executed at a very granular level. It demystifies the black box of modern processors, providing insights into performance bottlenecks, memory access patterns, and other low-level details that are often hidden from developers. It's essentially a debugger on steroids, helping developers optimize their applications like never before.
Popularity
Points 140
Comments 45
What is this product?
This project is an exploration and analysis of Apple's Processor Trace instrument, which provides detailed information about how a program runs on an Apple Silicon CPU. The project focuses on decoding the complex data generated by the instrument, allowing developers to understand the inner workings of their code at a very low level. This involves parsing the trace data, identifying specific instructions, and visualizing performance characteristics. The innovation lies in simplifying the interpretation of this raw data, turning it into actionable insights for developers.
How to use it?
Developers would use this by first enabling Processor Trace on their Apple Silicon devices (this usually involves specific developer tools and potentially some low-level configurations). Then, they'd run their application and capture the trace data. This project can then be used to process that data, analyzing the execution flow, identifying performance hotspots (areas of code that take the most time), and understanding memory access patterns. It provides a user-friendly interface to visualize the results. Developers can integrate this project into their existing debugging workflows or use it as a standalone tool for in-depth performance analysis. So, you can use this to find exactly where your code is slow and figure out how to make it faster.
Product Core Function
· Trace Data Parsing and Decoding: This function takes the raw trace data generated by the Apple Silicon processor and decodes it into meaningful instructions and events. This allows developers to understand exactly what the CPU is doing at each step. So this helps you understand what each line of code actually *does* in the CPU, so you can pinpoint problems.
· Performance Bottleneck Identification: This analyzes the decoded trace data to identify the parts of your code that are taking the most time, highlighting performance bottlenecks. This is a crucial step in optimization. So this helps you find out where your code is slow.
· Memory Access Pattern Analysis: This reveals how your code accesses memory, identifying potential inefficiencies like excessive memory reads or writes. Understanding these patterns can help developers optimize memory usage. So this helps you improve how efficiently your program uses the computer's memory, which can make it faster.
· Instruction-Level Analysis: Offers a detailed view of each instruction executed, including cycle counts, instruction type, and other performance metrics. This deep dive provides insights into the CPU's behavior. So this lets you see the exact steps the CPU is taking to execute your program, which is crucial for advanced debugging.
Product Usage Case
· Optimizing Game Engine Performance: A game developer uses the tool to identify slow rendering calls, and then optimizes those calls by re-writing the code. The project's analysis reveals that frequent memory allocations are slowing down the rendering process, prompting the developer to optimize memory management, resulting in a significant performance boost. So this can make your games run faster.
· Debugging a Network Application: A network application developer is experiencing high latency. Using the tool, they trace network calls and identify a bottleneck related to how data is processed. By analyzing the trace data, the developer identifies inefficient data processing logic, rewrites the code, and reduces latency significantly. So this can speed up network communication in your apps.
· Understanding CPU Usage in a Complex Application: A software engineer works on a complex application with multiple threads. Using the tool, they can examine the processor trace to see how different threads are interacting with the CPU, identifying potential concurrency issues and optimizing thread usage. So this can help you manage multiple tasks happening at once inside your program more effectively.
18
Blue-Collar Job Trend Analyzer: AI-Resilient Workforce Insights
Author
geox
Description
This project analyzes the recent trend of increasing popularity in blue-collar jobs, framed within the context of AI advancements potentially impacting office work. It doesn't directly build a tool, but provides a valuable perspective on how automation and AI are changing the job market, highlighting the resilience of skilled trades. It suggests a shift in career interests and investment strategies, focusing on sectors less susceptible to immediate AI disruption.
Popularity
Points 61
Comments 115
What is this product?
This isn't a software project in the typical sense. It's an analysis, a thought experiment. It leverages data about job market trends, especially the increasing interest in blue-collar professions (like construction, plumbing, electrical work). The 'innovation' lies in framing this trend as a response to the growing influence of AI in white-collar (office) jobs. So, instead of building a gadget, it's about understanding the shifts in the work landscape caused by AI, and offering insight into career pathways that might be more future-proof. This project is about understanding what the AI revolution means to us - especially those who need new jobs.
How to use it?
There isn't a specific application to 'use' in the traditional sense. The value lies in the insights. Developers and tech enthusiasts can use this analysis to inform their career choices, understand the potential impact of AI on various industries, and identify opportunities. You can integrate the findings into your personal financial planning, or in guiding others on their career paths. You could research similar trends in your local market using the same method. So, to 'use' it, you digest the ideas and consider their implications.
Product Core Function
· Trend Analysis: The core function is analyzing data related to job market trends, specifically focusing on the rising interest in blue-collar professions. This helps identify sectors less susceptible to automation. So what? This helps you understand which areas might be safer bets for your career, or for investing your time and money.
· AI Impact Assessment: This project implicitly assesses how AI might reshape the job market, distinguishing between roles at high and low risk of automation. This allows for informed decisions about career paths. So what? You get to avoid careers that are more likely to be taken over by machines.
· Career Guidance: The analysis implicitly provides insights and considerations for career planning, with an emphasis on the skills and professions that could be more resilient in an AI-driven future. So what? You can adjust your professional development goals, and find a career that is built to last.
· Investment Strategy: By understanding the potential effects of AI, the insights can inform investment choices and opportunities. So what? You can put your money where it will provide the most return, while helping support more secure industries.
Product Usage Case
· Career Re-evaluation: A software developer might, after reading the analysis, consider learning a skilled trade or investing in businesses in that sector. They understand that while coding skills are important, other professions might be in higher demand. So what? You can pivot to a more promising field.
· Business Startup: Someone looking to start a new company could use these insights to identify market gaps in blue-collar services, creating a business model less vulnerable to AI disruption. So what? You can build a business that can adapt to changes in the job market.
· Educational Planning: Parents and educators can use the analysis to guide students or children towards careers where the human element is essential, like trades or creative fields. So what? You can set up the next generation with skills that will last.
· Investment Portfolio Diversification: An investor might allocate a portion of their portfolio to companies providing services in blue-collar sectors, betting that these industries will remain strong. So what? You can protect your money and make smart investments.
19
Monday - The Thought Weaver
Author
brightbeige
Description
Monday is a fascinating project that explores the realm of personality generation and interaction through LLMs (Large Language Models). It's essentially an experiment in creating a digital 'personality' capable of engaging in dynamic, evolving conversations. The core innovation lies in how the personality is built and managed: by feeding the LLM curated textual data and iteratively refining its responses, the project aims to create a consistent, evolving digital persona. This addresses the common challenge of LLMs lacking sustained character or conversational coherence. It is designed to understand and adapt to user input.
Popularity
Points 81
Comments 92
What is this product?
Monday is a project that uses a computer program (LLM) to simulate a personality. It's not just about generating text; it's about building a digital identity that can adapt to conversations and maintain a consistent 'character.' The core idea is to train and refine the LLM based on its interactions, creating a more believable and engaging experience. So, it's like building a digital friend that gets smarter and more consistent over time.
How to use it?
Developers can interact with Monday by providing text input and observing the response from the LLM. You can see how the AI processes information and then responds, potentially using it to develop new chatbots or virtual assistants. The data and conversation with Monday can be fed back into the model to fine-tune the AI to behave as expected. So, you can explore how to make AI personalities more realistic and engaging.
Product Core Function
· Personality Generation: The project centers around the ability to create a digital persona using LLMs. This involves feeding the LLM with carefully selected data and iteratively refining its output. This means you can shape the responses to build a particular personality, and the character becomes more consistent over time. So, this lets developers create highly customized, personality-driven chatbots or virtual assistants.
· Iterative Refinement: The project uses feedback to train the AI for a more authentic feel. The project uses feedback to adjust and refine the responses generated by the model, ensuring consistency and coherence. It provides a method to improve the AI. So, you can improve the quality of your AI's interactions and maintain character.
· Dynamic Interaction: The project has a capacity to engage in dynamic and adaptive conversations. This means the AI can respond to user input and adjust its style and content accordingly. So, this allows the construction of very interactive and engaging AI-driven applications.
Product Usage Case
· Chatbot Development: You can use this technology to create highly personalized chatbots for customer service, or virtual assistants for various applications. For example, a company could create a chatbot that interacts with customers with a distinctive brand personality.
· Interactive Storytelling: The project can also be used in game development, providing characters with rich, and engaging personalities. It will help the characters react to the players' input and create a unique story. So, you get the ability to make your stories and games much more interactive.
· Educational Tools: You could use this to develop educational tools where an AI tutor has a specific persona and tailored responses to support different learning styles. So, users can have personalized, engaging educational experiences.
20
OfficeQuiet: Noise-aware Productivity Optimizer
Author
skrid
Description
OfficeQuiet is a tool designed to combat the distractions of open-plan office environments. It analyzes background noise levels in real-time and dynamically adjusts user's task assignments based on the current noise landscape. This provides a personalized productivity experience. The project's technical innovation lies in its real-time audio analysis combined with task scheduling. It leverages audio analysis to interpret the environmental noise, and uses this to optimize task allocation, giving employees a better experience to focus on their work.
Popularity
Points 81
Comments 76
What is this product?
OfficeQuiet listens to the sounds around you and figures out how noisy it is. It uses the information about the noise level to help you do your work better. Imagine a program that actively adapts to the environment. It does this by analyzing the audio, detecting when it's quiet or loud and then suggesting tasks which match those conditions. This is innovative because it proactively manages the employee's focus, enhancing the ability to work efficiently in a distracting environment.
How to use it?
Developers can potentially integrate OfficeQuiet into their existing productivity or task management tools. It could be integrated into a personal assistant app, a project management system, or even a browser extension. The integration would involve capturing audio input from the user's environment and feeding it into the application to get real-time noise analysis. It can then be used to guide the task assignment and provide personalized recommendations to the user. So developers can use OfficeQuiet to build smarter productivity tools, that consider environmental factors.
Product Core Function
· Real-time Audio Analysis: This function monitors the surrounding sounds, detecting speech, keyboard typing, or other distracting noises. The value is in its ability to quantitatively assess the noise level and identify when the environment is disruptive. So this helps your productivity tool understand what is distracting the user.
· Adaptive Task Scheduling: This feature assigns tasks based on the noise levels. In a quiet environment, it might suggest focusing on deep work. In a loud environment, it could suggest tasks like emails. This adaptive scheduling helps optimize productivity. It learns what task best fits the noise around.
· Personalized Profiles: The system can learn user's preferences and work habits. By doing so, it can customize task suggestions. If you prefer working on coding when there's a lot of noise, it will learn that and provide you with more coding tasks. So this means a more tailored and effective way to work, specific to your individual style.
· Notification and Alerting: It provides gentle reminders to switch between tasks or inform the user of potential noise disturbances. So, these notifications help keep the user's focus on the task at hand.
Product Usage Case
· In a busy open-plan office, a developer is struggling to concentrate on a complex coding task. OfficeQuiet detects the noise levels and recommends simpler tasks or more 'focus-friendly' work like documentation or bug fixes. The developer could then focus on the less demanding job to allow their mind to rest. This helps developers get through their day.
· A project manager in a coworking space is constantly interrupted by conversations and other ambient noise. OfficeQuiet detects loud noise and advises on less-demanding tasks. This allows them to stay productive and focused while still getting work done. So the project manager is more productive because their day is better managed by the tool.
21
99Lisp: A Tiny Lisp Interpreter
Author
shikaan
Description
99Lisp is a minimalistic implementation of the Lisp programming language, achieved in just 99 lines of code. It demonstrates the elegance and power of Lisp by encapsulating a complete language interpreter within a surprisingly small footprint. The project focuses on parsing, evaluation, and basic data structures, providing a compact yet functional Lisp environment. It showcases how core programming concepts can be distilled and understood through concise, well-structured code. This project also highlights how a simple foundation can be built to understand and extend the functionalities of a whole programming language.
Popularity
Points 105
Comments 26
What is this product?
99Lisp is a fully functional Lisp interpreter – a program that executes instructions written in the Lisp programming language – built using only 99 lines of code. It does this by implementing the core components of a programming language: a parser (which translates human-readable code into something the computer understands), an evaluator (which figures out what the code means and what to do), and fundamental data structures. The innovation lies in its extreme conciseness, proving that a complex language like Lisp can be implemented with surprisingly few lines of code. So what does this mean? It's a testament to how powerful and well-structured Lisp and its related concepts can be; it also allows for an in-depth understanding of these principles by simply dissecting the code.
How to use it?
Developers can use 99Lisp to learn how interpreters work, to understand the underlying principles of the Lisp language, or to experiment with language design. Because it’s simple, it can be modified and extended easily. You could integrate it into other projects as a basic scripting engine if you needed a lightweight language to run alongside your primary application. To use it, you'd feed it Lisp code. Think of it like feeding instructions to a very simple, specialized computer. So, for example, this might be useful if you're a game developer and need a simple scripting language for your games.
Product Core Function
· Parsing: The ability to transform human-readable Lisp code into a format the computer can understand. This is a fundamental part of any programming language implementation and allows us to take written Lisp expressions and prepare them for interpretation. So what does this mean? This allows you to input code, like mathematical formulas or instructions, and have the program understand what you’re asking it to do.
· Evaluation: The core process of interpreting and executing Lisp code. This function takes parsed code and determines its meaning and then runs it. So what does this mean? It's what actually makes the Lisp code *work* – if you write code to add two numbers, the evaluator does the actual addition.
· Basic Data Structures: Implementations of fundamental data types like lists, which are the building blocks of Lisp programs. So what does this mean? Lisp uses lists for data storage and function calls, allowing for incredibly flexible and dynamic programming.
Product Usage Case
· Learning: It provides a concise example for those learning about interpreters or wanting to understand Lisp. You can actually *see* how the language works under the hood. So what does this mean? You get a deep understanding of how Lisp is built – perfect for aspiring language designers.
· Experimentation: Developers can use 99Lisp as a base for experimenting with their own programming language features or modifying Lisp. You can add functions or change how the language operates, essentially designing your own version. So what does this mean? You can explore language design principles without a huge time investment.
· Education: It can be integrated into computer science courses to teach fundamental concepts like parsing, evaluation, and data structures in an easily digestible way. So what does this mean? It's a fantastic tool for teaching students about the core principles of programming languages.
22
unsafehttp - A Barebones Web Server in C
Author
GSGBen
Description
This project is a minimal web server written entirely from scratch in the C programming language. The developer built it to learn the intricacies of C programming, Unix socket programming, and the compilation process. The server runs on a small single-board computer, striving for simplicity and direct communication. This allows for deep understanding of how web servers function at the lowest level, bypassing layers of abstraction commonly found in more complex server software. This project highlights a 'back-to-basics' approach, focusing on direct control and granular understanding of networking protocols and system interactions. So this is useful because it teaches you how a web server actually works under the hood, which can help you debug issues and optimize performance.
Popularity
Points 80
Comments 48
What is this product?
It's a very basic web server, built in C, using low-level network programming (sockets). It doesn't rely on pre-built frameworks. Instead, it directly handles incoming web requests (like your browser asking for a webpage), processes them, and sends back the requested data. The innovation here lies in its simplicity. It's a minimalist approach, designed to demonstrate the fundamental principles of web server technology, removing the complexity of existing frameworks. So, this means you learn the core concepts without getting lost in extra features.
How to use it?
Developers can use this as a learning tool to understand the inner workings of web servers. They can study the source code to learn about socket programming, HTTP protocol handling, and other low-level networking concepts. Additionally, it can be used as a foundation for building custom web servers with very specific functionalities, or as a base for testing and experimenting with different network configurations. So this is useful for anyone who wants to really understand networking and build custom tools.
Product Core Function
· Handles HTTP requests: The server receives and parses HTTP requests from clients (like web browsers). This involves understanding the HTTP protocol, including request methods (GET, POST, etc.), headers, and the data being sent. This helps you see how your browser asks for a webpage, and understand the data exchange process.
· Serves static content: The server is able to retrieve and serve static files (like HTML, CSS, and images) from the file system. This demonstrates the ability to respond to client requests with predefined data. This shows you how your browser gets the files that create a webpage.
· Socket programming implementation: It leverages socket programming in C to establish network connections, listen for incoming requests, and send responses. This provides a practical insight into how network communications are handled. This lets you see exactly how a computer talks to the internet.
· Minimal dependencies: Built with very few external libraries, emphasizing the use of standard C libraries and system calls. This gives you complete control and understanding of how the server functions. This is important because it avoids unnecessary overhead and dependencies, which allows for better performance.
Product Usage Case
· Educational tool for network programming: Developers can study the source code to learn about socket programming, HTTP protocol handling, and other low-level networking concepts. It’s like taking a networking course with the source code as the textbook. So this helps you understand how the internet works.
· Custom web server development: It provides a base for building custom web servers with very specific functionalities, like handling unusual requests or special content. You can tailor the server exactly to your needs. So this gives you more control over your web applications.
· Experimentation with networking configurations: Use it to test and experiment with different network configurations, such as handling various protocols, security settings, or resource management. This allows you to test different network designs. So you can create more efficient and secure network systems.
· Debugging and troubleshooting: Because of its simplicity, it is easier to debug and understand the cause of any issues. So, if there are any bugs, you can easily figure out what is going on.
23
FlagCross: A Semantic Analysis Tool for Identifying Ideological Rhetoric
Author
douchecoded
Description
FlagCross is a project leveraging Natural Language Processing (NLP) techniques to analyze text and identify potentially problematic ideological rhetoric, specifically focusing on patterns often associated with certain political ideologies. It uses techniques like keyword extraction and sentiment analysis to flag text that might be conveying such messaging. The core innovation lies in its ability to proactively identify and flag content that might be subtly promoting ideologies through language, rather than just focusing on blatant hate speech. This addresses the problem of hidden ideological influence in written communication.
Popularity
Points 82
Comments 38
What is this product?
FlagCross works by taking a piece of text and breaking it down. It looks for specific words and phrases commonly used by certain groups, and also assesses the overall 'feeling' or sentiment of the text. If it finds patterns that match those used by problematic ideologies, it flags the text as potentially concerning. It's like a digital language detective, searching for clues of hidden agendas. The innovation is that it's not just looking for obvious hate speech, but also subtle clues in the language that can hint at underlying ideological biases. So what? This helps you understand the true meaning behind the words, even when it's not immediately obvious.
How to use it?
Developers can use FlagCross as a tool within larger applications. Imagine integrating it into a content moderation system for social media, a news aggregator, or even an educational platform. To use it, a developer would typically pass a text string (like a social media post or an article) to FlagCross's API. The API would then return a score indicating the likelihood of ideological messaging, along with specific phrases or sentences that triggered the flag. You can use this to automatically flag content, alert moderators, or provide users with context about the potential implications of the text they're reading. So what? This provides a way to better understand and manage the spread of potentially harmful content.
Product Core Function
· Keyword Extraction: This function identifies and highlights specific words and phrases that are often associated with particular ideological groups. The technical value is in its ability to quickly spot potential red flags in a text. The application is in content moderation, where it can automatically flag content that uses sensitive terminology, alerting human moderators.
· Sentiment Analysis: This analyzes the emotional tone of the text – is it positive, negative, or neutral? By looking for patterns of emotion, the tool can identify if the message is trying to manipulate the reader's feelings. The technical value is in its ability to assess the persuasive techniques used in the text. Its application lies in detecting propaganda and understanding the underlying intent of a communication.
· Contextual Analysis: This analyzes the surrounding text of potentially problematic phrases to determine if their use is intended in an ideological way. The technical value here is its understanding of nuance – recognizing the context in which words are used. The application can filter out false positives in content moderation to give more accurate result.
· Reporting & Scoring: This provides an overall score indicating the likelihood of problematic ideological messaging, along with explanations for the flags. The technical value is in summarizing complex analysis into an actionable result. It can be applied in any content moderation system to better understand and manage the spread of potentially harmful content.
Product Usage Case
· Social Media Moderation: A social media platform integrates FlagCross to automatically flag posts that use specific keywords or phrases related to ideologies. So what? This improves the speed and accuracy of content moderation, reducing the need for manual review and protecting users from exposure to potentially harmful content.
· News Article Analysis: A news aggregator uses FlagCross to analyze articles and provide users with context about the potential ideological bias. So what? Users are provided with more information to critically assess the information they are receiving, helping them to make informed decisions.
· Educational Resources: A educational platform integrates FlagCross to analyze student's essays to flag potential ideological bias. So what? Students can use the feedback to reflect on their writing, and instructors can use it to understand student's thought process.
24
Creatine Insights: A Personalized Supplement Recommendation Engine
Author
Anon84
Description
This project, analyzing a Hacker News discussion about creatine, aims to provide insights into the supplement's use. It doesn't offer a direct tool, but rather demonstrates the potential of analyzing textual data (like HN discussions) to extract useful information and formulate informed opinions. It's not about building a creatine tracking app, but showcases the power of understanding and processing information in the realm of health and wellness.
Popularity
Points 39
Comments 69
What is this product?
This project leverages the content of an online discussion (in this case, a Hacker News thread about creatine) to highlight key perspectives and user experiences. It doesn't analyze chemical composition, but focuses on the human conversation. The innovation lies in applying natural language processing (NLP) techniques to extract sentiment, identify popular opinions, and synthesize them into a digestible overview. So, this is like a smart summary engine, tailored to health-related discussions, instead of just showing you every comment, it shows you the key information.
How to use it?
You wouldn't 'use' this project directly as a consumer tool (at least in its presented form). However, developers can use the underlying principles – like topic modeling and sentiment analysis – to build tools that process and summarize any text-based data. Imagine applying these techniques to product reviews, customer feedback, or scientific publications. So, imagine this as a building block. If you want to know what people think about a product, this can show you the key opinions.
Product Core Function
· Sentiment Analysis: The system identifies positive, negative, and neutral opinions expressed within the HN thread. This helps to understand the general consensus regarding creatine and its effects. This information helps you understand the general mood around the topic: are people excited, skeptical, or neutral? So, this helps you quickly understand the overall reaction.
· Topic Modeling: The project identifies the key discussion points within the thread, such as dosage, side effects, different brands, and personal experiences. This gives a structured overview of the creatine discussion. So, this shows you the main things people are talking about.
· User Role Identification (hypothetical): The system could potentially infer the role of each commenter (e.g., expert, user, researcher) based on their language and background. This helps to weight opinions based on the source. So, it could indicate whose opinions might be more valuable.
· Summarization: The project aims to condense the information into a concise summary that captures the main arguments and viewpoints. This allows users to quickly grasp the salient points without reading the entire thread. So, it gives you the gist of the discussion without having to read every comment.
Product Usage Case
· Product Reviews Analysis: A developer could use these techniques to analyze customer reviews for a health supplement, identifying common complaints and praises to improve product offerings and marketing. So, this is useful for a company to improve their product.
· Medical Literature Review: Researchers can process scientific papers, using similar methods, to quickly identify key findings, trends, and disagreements within a specific medical field. So, researchers will be more efficient with their reading.
· Personalized Health Recommendations: This approach can be applied to personalize health recommendations based on individual's health profile and online discussions. So, you get health insights related to your profile.
25
Engineer-First Mindset Explorer
url
Author
JumpCrisscross
Description
This project isn't a tangible product, but rather an observation and analysis of how engineering-focused leadership, as seen in China, differs from the legal-focused leadership often found in the US. It highlights the potential advantages and disadvantages of each approach, focusing on technological innovation and rapid iteration. The core idea is: prioritizing engineers can lead to faster technological development and a more proactive problem-solving culture, while an overemphasis on legal aspects might slow down innovation due to risk aversion and a focus on existing regulations.
Popularity
Points 56
Comments 39
What is this product?
This isn't software; it's an observation and a thought experiment. It explores how different leadership philosophies impact a nation's technological advancement. It compares two models: one where engineers hold significant power and influence, fostering a culture of building and iteration, and another where lawyers and legal considerations are prioritized, potentially slowing things down. The innovation lies in the comparative analysis of leadership styles and their effects on technological progress, using China and the US as case studies.
How to use it?
There's no direct usage in terms of code or software. Instead, this is for anyone interested in leadership, technology, and national strategies. You use this by reflecting on the contrasting approaches and considering their implications for your own project or company. How can you apply the lessons learned – perhaps fostering an environment that values engineering and rapid experimentation?
Product Core Function
· Comparative Analysis: Comparing the leadership styles of engineers versus lawyers. The value is understanding the cultural differences that shape innovation. This helps people think about how to structure their teams to prioritize technological innovation and encourage a proactive approach to problem-solving. It can be used to understand how to improve a project's direction by prioritizing the engineers that have the right knowledge.
· Identifying Core Values: Emphasizing the role of engineers in driving technology innovation and their importance in project development and company goals. The value is recognizing which team members should have the most authority in decision-making. This is useful when developers are starting a project and need to think through their teams responsibilities.
Product Usage Case
· For entrepreneurs: Understanding the potential trade-offs between speed of innovation and legal compliance can help make informed decisions. For instance, launching a Minimum Viable Product (MVP) quickly and iterating based on user feedback (a core engineering principle) might be prioritized over meticulously navigating all legal hurdles upfront. So this is useful for making decisions that will help your project's technological innovation.
· For technology leaders: Applying the principles to your own organization. By prioritizing engineers in decision-making processes and fostering a culture of experimentation, you can accelerate innovation. This is useful because it provides insight into the value of allowing engineers to make important decisions in companies.
26
BreezeIconFix: A KDE Theme Customization Tool
Author
bundie
Description
This project addresses the issue of KDE removing colorful third-party app icons from its Breeze icon theme. It's a tool to help users customize their desktop environment by allowing them to restore and maintain these colorful icons, effectively providing a workaround for the changes in the default KDE theme. The core innovation lies in its ability to automatically identify and patch the icon mappings, ensuring a personalized and visually appealing desktop experience.
Popularity
Points 29
Comments 58
What is this product?
This is a utility that allows users of the KDE desktop environment to preserve and manage colorful application icons that were removed from the default Breeze icon theme. It works by identifying and patching the configuration files that control how icons are displayed, ensuring that third-party application icons retain their original colors and designs. This project showcases a solution for maintaining user preferences and customizing the appearance of their desktop, even when core system components change.
How to use it?
Developers can use BreezeIconFix by installing it and running it within their KDE environment. It will automatically scan for and apply the necessary patches. This is particularly useful for users who rely on specific colorful icons for their applications and want to ensure that their desktop maintains its familiar look. The integration typically involves running the tool after a KDE update or when the theme is changed.
Product Core Function
· Icon Patching: The core function is to modify system configuration files (specifically icon theme configuration) to map application icons to their colorful counterparts. So, this ensures that the original icons are displayed instead of the new, potentially less visually appealing ones. This is useful if you want to keep your icons looking the way you like them and not be forced to change when the system updates.
· Automated Icon Detection: The tool intelligently identifies the icons of installed applications, making the patching process seamless. It scans the file system and configuration files to find the appropriate icon locations. So, this saves users from having to manually locate and specify each icon, making the process much more user-friendly.
· Theme Compatibility: BreezeIconFix aims to be compatible with different KDE themes, adapting its patching mechanism to work across various theme configurations. This means it can be used with other icon themes, providing more customization options for users. This increases the tool's usability and adaptability.
· Update Resilience: The tool is designed to withstand future KDE updates. It is designed to re-apply the patches if needed, making sure your chosen icon setup remains consistent. So, you do not need to worry that your customizations get overwritten with the new update.
· User Interface: The tool may include a simple user interface (if not command-line only) to facilitate the patching and management of the icon configurations. This simplifies the customization process for non-technical users. It allows users to easily manage their icon settings without delving into the command line.
Product Usage Case
· Customizing the Desktop Appearance: A user wants to maintain a consistent visual appearance of their desktop across system updates, including the icon theme. They use BreezeIconFix to restore the original colorful icons and keep their desktop looking the way they like it.
· Preserving Icon Customization: A developer has a specific workflow that relies on being able to visually distinguish applications by their icons. BreezeIconFix is employed to ensure that this customization is maintained after system updates or theme changes.
· Workaround for Design Changes: When the KDE project changes its icon theme (such as removing color), a user uses BreezeIconFix to prevent the default theme from overwriting their preferred icon style, offering an alternative for users dissatisfied with the new changes.
· Theme Management in Development: A developer is creating their own customized theme for their development setup. They can utilize this tool to manage the application icon mapping in their own customized icon theme.
· Supporting Accessibility: A user with visual impairments may rely on certain icon color schemes. BreezeIconFix ensures the retention of these critical visual cues.
27
Contextual Alerting System (CAS)
Author
nujabe
Description
This project isn't a typical software tool; it's more of a conceptual exploration around how to filter and prioritize alerts, especially in high-noise environments. It simulates a system designed to detect and analyze patterns related to cybersecurity threats, specifically looking at real-time data to identify potential malicious activities, using probabilistic reasoning. It tries to reduce the number of false positives, focusing on what's truly important in complex security scenarios.
Popularity
Points 41
Comments 21
What is this product?
CAS is a hypothetical system, imagine it like a super smart alarm system for your computer network. Instead of just shouting 'something's wrong,' it carefully analyzes everything happening and tries to figure out if there's a real danger. It uses some really clever math – probabilistic reasoning – to estimate the chances of a problem being a real threat. The innovation is in the filtering and prioritization of alerts, attempting to cut through the noise to focus on what matters most. So it's like having a security guard that's actually good at its job by making smart decisions.
How to use it?
Since this is a concept project, there's no direct way to 'use' it as a ready-made tool. However, a developer could learn from its approach. Think of it as a blueprint for building a system that filters security alerts. If you're working on a security monitoring tool, you could use the ideas here to improve how you handle alerts. You might use its insights to prioritize alerts based on context, and you can incorporate risk factors into your system. You would integrate the idea of probabilistic reasoning into your data analysis pipeline.
Product Core Function
· Probabilistic Reasoning for Threat Assessment: It uses advanced math to calculate how likely a detected problem is to be a real threat. So this helps in reducing false alarms, and lets you focus on the real issues. This will make your security system less noisy and more effective.
· Contextual Data Analysis: It looks at the whole picture – what's happening on the network, who's doing what, when. This helps the system understand the context of a potential threat. This means your system is smarter and less likely to miss things.
· Alert Prioritization: It ranks threats based on how serious they are. This allows you to deal with the most dangerous problems first. This means saving time and resources, focusing on the most important threats.
· Pattern Recognition: It recognizes specific patterns indicative of malicious activities, focusing on specific attack vectors. This lets the system quickly spot the typical signs of cyberattacks. This means detecting the attacks earlier and reducing the possible damage.
Product Usage Case
· Security Information and Event Management (SIEM) System Enhancement: The core ideas of CAS can be applied to existing SIEM systems, enabling more intelligent alert filtering and prioritization. You could apply this to filter thousands of alerts from the logs and focus on the important ones.
· Network Intrusion Detection System (NIDS) Improvement: Implement contextual data analysis to improve the accuracy of NIDS. Using this the system would know if a particular network activity is malicious.
· Incident Response Automation: Use the alert prioritization strategies of CAS to automate the incident response process, helping security teams respond faster and more effectively. Imagine a scenario where a high-priority threat is detected, and the system automatically blocks the IP address from connecting to the network. This saves time and minimizes damage.
28
EchoWave: Building Wireless Networks with Microwave Repeaters
Author
BallsInIt
Description
EchoWave provides a way to extend the range of wireless networks by using passive microwave repeaters. The project focuses on reflecting and amplifying microwave signals without active electronics, offering a potentially more resilient and cost-effective solution for communication in challenging environments. It addresses the limitations of traditional wireless technologies, particularly in situations where power and infrastructure are scarce. The core innovation lies in the design and implementation of these passive repeaters, enabling long-distance communication with minimal resources.
Popularity
Points 52
Comments 9
What is this product?
EchoWave is essentially a method of bouncing microwave signals off reflectors, like giant mirrors, to extend the reach of a wireless network. Instead of using complex electronic equipment to amplify the signal, it relies on strategically placed reflectors. This approach simplifies the technology and can be more robust. Think of it like using a mirror to direct sunlight further than it would naturally go. It’s innovative because it provides a low-power and possibly cheaper way to build a wireless network, especially in remote locations where setting up typical wireless infrastructure is difficult.
How to use it?
Developers can use EchoWave by designing and deploying these microwave reflectors. They would determine the strategic placement of the reflectors to bounce the signals over long distances or around obstacles. This would involve considerations like the signal frequency, the reflector's shape and material, and the surrounding environment. The use cases are for situations where conventional wireless methods are not feasible – in disaster relief, remote sensing, or rural areas where setting up base stations might be difficult or very expensive.
Product Core Function
· Microwave Signal Reflection: This is the core function. The repeaters passively reflect the microwave signal, acting like a mirror for radio waves. This allows the signal to travel further and circumvent obstacles. So what? This allows you to build wireless networks in areas where it was previously impossible, like between buildings, over hills, or in areas with limited power sources.
· Passive Operation: The system requires no power at the repeater itself, leading to a more reliable and potentially less expensive solution. This makes it ideal for areas where power is unreliable or inaccessible. So what? This means you can deploy communication systems in places like disaster zones, where traditional infrastructure might be damaged or destroyed.
· Range Extension: The primary goal is to extend the range of wireless communication. By reflecting the signal, it allows communication over longer distances without needing a signal booster. So what? This opens up possibilities for communication in remote areas, or for providing wider coverage in areas with challenging terrains.
Product Usage Case
· Disaster Relief: Deploying EchoWave repeaters after a natural disaster to quickly re-establish communication lines between rescue teams and affected communities. The passive nature of the repeaters means they are less likely to fail during a power outage. So what? This helps with fast communication in emergencies, where every second counts.
· Rural Internet Access: Setting up EchoWave repeaters to provide internet access to remote villages, where traditional wired or cellular infrastructure is unavailable or too expensive. So what? This helps bridge the digital divide, providing internet to underserved communities.
· Industrial Monitoring: Use EchoWave to create wireless links for sensor data transfer in industrial environments with physical obstructions or RF interference. The system is robust to handle noisy or difficult signal environments. So what? This means better monitoring and control in manufacturing plants or automated systems.
29
PG Auto Upgrade - Self-Updating Postgres in Containers
Author
justinclift
Description
This project provides a Docker (and Kubernetes) container that automatically upgrades your PostgreSQL database. It tackles the common problem of keeping your database up-to-date with the latest security patches and features, simplifying a historically manual and complex process. It automates the upgrade process, reducing downtime and ensuring you're running the most secure and performant version of PostgreSQL. So this helps you maintain a secure and performant database without manual intervention.
Popularity
Points 15
Comments 4
What is this product?
It's a Docker container designed to automatically upgrade your PostgreSQL database. Behind the scenes, it uses a combination of scripting and the standard PostgreSQL upgrade tools (like `pg_upgrade`) to move your data and settings to a newer version. The innovative part is the automation; it monitors your database version and, when a new version is available, handles the entire upgrade sequence, making sure your data is migrated correctly. So this is a hands-free way to keep your database current.
How to use it?
Developers would typically deploy this container alongside their existing PostgreSQL container. You'd configure it to monitor the database, and it would handle the upgrade process when a new PostgreSQL version is released. This might involve specifying the database connection details and setting an upgrade schedule. It's integrated by simply linking it to your existing database container, and letting it do the work. So this integrates seamlessly with your current setup to provide automatic upgrades.
Product Core Function
· Automated Version Monitoring: The container constantly checks for new PostgreSQL versions. This uses public PostgreSQL repositories to get updated versions. The value is always running the latest and most secure database versions; the application automatically gets updated to the latest versions, which helps with security and performance improvements. For example, you'll always have the latest features and security fixes.
· Data Migration Handling: When a new version is found, it automatically manages the migration of your data to the upgraded version using `pg_upgrade` or similar tools. This ensures your existing data is preserved. This saves time and effort involved in manually migrating data after an upgrade. For example, it makes upgrading across major PostgreSQL versions a lot easier.
· Rollback Capabilities: Implements mechanisms to handle failed upgrades, potentially rolling back to the previous version. This adds a layer of safety and prevents data loss. This protects you from potential data loss and gives you a chance to troubleshoot if the update fails. For example, it can restore your database to its previous state if the upgrade fails.
· Containerized Deployment: Packaged as a Docker container for easy deployment and orchestration in environments like Kubernetes. This allows for easy deployment in many environments. For example, it works seamlessly in your Kubernetes cluster or cloud environments.
Product Usage Case
· Continuous Integration/Continuous Deployment (CI/CD) Pipelines: Integrating this container into CI/CD pipelines. After the new upgrade, database schema is changed to adapt to the new changes. This allows developers to receive instant notifications about updates, and automatic deployment can be handled during off-peak hours. So you can keep your database fresh and safe, always.
· Kubernetes Deployments: Easily deploying PostgreSQL in a Kubernetes environment, with the upgrade container managing upgrades automatically. When a new version is released, the update is done by itself without stopping the service for a long period of time, thus saving engineers a lot of manual work. So you have automated database upgrades with minimum downtime in a Kubernetes setup.
· Cloud Database Management: Using this container in a cloud environment for easy upgrades and management of your database. This simplifies the maintenance and upgrades of a database system in your cloud. For example, you can apply upgrades during weekends automatically.